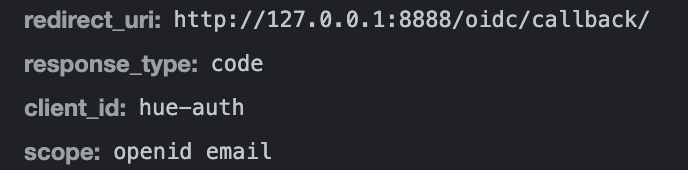
Hello,
I am currently trying to integrate an OIDC authentication backend for Hue (image : 4.7.0) that interacts with our in house SSO client that provides tokens to the Hue application.
Hue is able to navigate to the oidc_op_authorization_endpoint for my configured value but i see its not taking the redirect login url which am passing. I narrowed down that it seems to be failing due to the redirect uri defaulting to localhost, the authentication api fails saying invalid uri. I defined a login_redirect_url, like the example in hue.ini as seen below.
Please kindly suggest how to override this value.
FYI : We are using official hue helm chart which comes with default nginx (we aren’t modifying any configs for nginx). However we have an ingress config for default url which is also mentioned below.
[[oidc]]
# The client ID as relay party set in OpenID provider
oidc_rp_client_id=hue-auth
# The client secret as relay party set in OpenID provider
oidc_rp_client_secret=*****tSOdhkYDlxSOqelxfpQcxQX
# The OpenID provider authoriation endpoint
## oidc_op_authorization_endpoint=https://keycloak.example.com/auth/realms/Cloudera/protocol/openid-connect/auth
oidc_op_authorization_endpoint=https://flying-kraken.id3.uat.cloud.**.net/api/v1/domains/***/openid-connect/auth
# The OpenID provider token endpoint
oidc_op_token_endpoint=https://flying-kraken.id3.uat.cloud.**.net/api/v1/domains/***/openid-connect/token
# The OpenID provider user info endpoint
oidc_op_user_endpoint=https://flying-kraken.id3.uat.cloud.**.net/api/v1/domains/***/openid-connect/userinfo
# The OpenID provider signing key in PEM or DER format
## oidc_rp_idp_sign_key=/path/to/key_file
# The OpenID provider authoriation endpoint
oidc_op_jwks_endpoint=https://flying-kraken.id3.uat.cloud.***.net/api/v1/domains/***/openid-connect/certs
# Whether Hue as OpenID Connect client verify SSL cert
oidc_verify_ssl=false
# As relay party Hue URL path to redirect to after login
login_redirect_url=https://hue-pras0004.use.eks.arch.sip.dev.cloud.***.net/oidc/callback/
# The OpenID provider URL path to redirect to after logout
logout_redirect_url=https://flying-kraken.id3.uat.cloud.**.net/api/v1/domains/**/openid-connect/logout
# As relay party Hue URL path to redirect to after login
login_redirect_url_failure=https://hue-pras0004.use.eks.arch.sip.dev.cloud.**.net/hue/oidc_failed/
# Create a new user from OpenID Connect on login if it doesn't exist
create_users_on_login=true